Website Pentesting
Website Security
Your Website represents your business digital identity in today’s information era. It gives your business a face, and defines your ideology to the world. A website can become a prime target of any hacker. Newbies and experts will try to attack a website for several reasons. Businesses often have only one chance to make a first impression to their customers, and your website is sometimes your only chance. If a customer visits your website and finds that it has been flagged as potentially harmful, the impression could be negative, and that customer may never return.
We offer comprehensive website penetration testing services that involve a highly complex website security testing procedure. Our experts will identify and attempt to exploit known and unknown weaknesses that are hidden within your website.
We conduct all website security tests to the highest standards and follow the OWASP website penetration testing framework and guidelines.

Methodology
Here at Mudbrix Consultancy, we employ the use of automated and manual tests to ensure all vulnerabilities can be identified before any hacker takes advantage.
Automation:
We use the best tools to test your web site for known vulnerabilities. While using Automated tools, we also make sure your website is not accidentally taken down (DOS).
Manual:
We test all vulnerabilities listed in automated scanning to remove false positives. All automated tools have limitations, so after automated testing, we repeat the process manually to make sure no stone is left unturned.
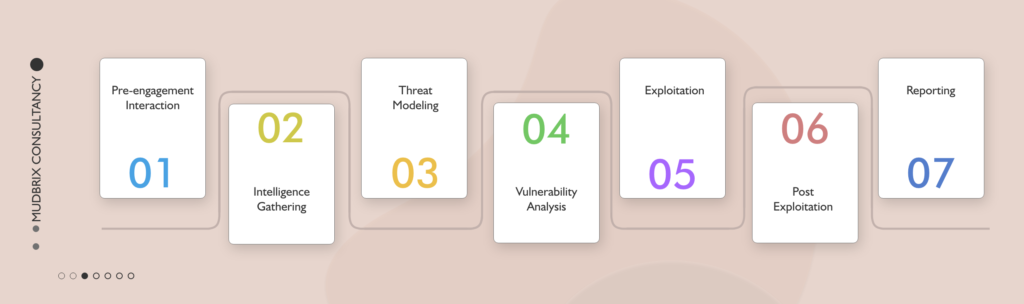
Our Approach
- Information gathering
- Crawling
- Exploitation
- Post Exploitation
- Information analysis
- Reporting
What you get?
- Security Lock
- We will provide 2 reports for every scan performed
Detailed Report – This is a technical report after completion of the pentest. The report will highlight weaknesses in the Web Application that affect the availability, reliability and integrity of information assets. It will also provide solutions for covering each identified risk. Your report will contain the following:
Categorization of weaknesses based on risk level
Details of security holes discovered
Emergency quick-fix solution for discovered vulnerabilities
Executive Report– It provides a bird eye view for the complete assessment done, and contains overall details of the identified vulnerabilities, operational impact of each vulnerability, potential financial impact along with the criticality of identified gaps. It also provides suggested priorities for the patch work.

